Solaris Jumpstart – howto guide
Setup and configuration of jumpstart server & clients .
Jumpstart offers a way to install Solaris using network over multiple server with similar of different configurations.
Here is a step by Step howto guide to install Solaris over network .
1.0 Before you start
Pre Installation Checklist :
* The install server or boot server is in the same local network segment as client with network link up .
* NFS services are running On jumpstart server
* The tftp services are running . To start uncomment the tftp entry in /etc/inet/inetd.conf and restart the inet services
* The reverse address lookup daemon ,in.rarpd , is running .
2.0 Preparing for a jumpstart server
Create and share a directory to store and share install server data.
#mkdir /export/install
share it
#vi /etc/dfs/dfstab
add share -F nfs -o ro,anon=0 /export/install
to export file system for sharing.
Do a shareall so that the file system is now exported
2.1 Setting up an Install server
Mount Solaris cdrom
Follow the steps :
#cd /cdrom/cdrom0/s0/Solaris_2.7/Tools
#./setup_install_server /export/install
This will copy the cdrom contents in to the /export/install directory.
2.2 Setting up a boot server
For installing clients over different networks you need a boot server in the same subnet as client .
Boot server after booting the client hands over subsequent installation & configuration process to install server .
# ./setup_install_server -b /export/install sun4u
the above command installs software for booting the client.
You also have to do a add host and add_install_client in boot server, see adding clients . Rest of the configuration has to be done at install server.
2.3 Setting up configuration files
Make a jumpstart directory say /jumpstart
Copy sample jumpstart files from cd
#cp –r /cdrom/cdrom0/s0/Solaris_2.7/Misc/* /jumpstart
2.4 Making Rules
Edit the sample rules file as per your requirement
#vi /jumpstart/rules
Keywords their value and usage is described in rules file itself.
any minus sign (-) in rule value always matches for that keyword.
RULE_KEYWORD RULE_VALUE DESCRIPTIONS
domainname text system’s domain name
disksize text range system’s disk size
disk device name text disk size (MBytes range)
hostname text system’s host name
installed text text system’s installed ver. of Solaris disk device name (text)
OS release text
karch text system’s kernel architecture
memsize range system’s memory size (MBytes range)
model text’ system’s model number
network text system’s IP address
totaldisk range system’s total disk size (MBytes range)
The following rule set matches any machine and redirect the install request to a profile file called any_machine.
any – - any_machine -
more examples can be found in rules file.
2.5 Verifying rules
A script called check validates and generates a rules.ok file if syntax, keywords are in order.
#./check
Validating rules…
Validating profile any_machine…
rules ok.
The clients will read the rules.ok file for booting information
2.6 Creating Profiles
Profile is a text file which contains configuration information for the clients
A sample profile file called any_machine is already there . You can create your custom profile files through text editor and mention in rules file.
#vi any_machine
install_type initial_install
system_type server
partitioning explicit
filesys c0t0d0s0 500 /
filesys c0t0d0s1 1000 swap
filesys c0t0d0s3 1000 /usr
filesys c0t0d0s4 1000 /var
filesys c0t0d0s5 1000 /opt
cluster SUNWCall add
2.7 Sysidcfg file
Sysidcfg file keeps the various system information like locale time zone etc and supply it to the client at the booting time. In the absence of this the installation turns in to interactive mode to prompt you to supply the value for these variables
You have to create this file in text editor . A sample file would look like following
# vi sysidcfg
system_locale=en_US
install_locale=en_US
timeserver=localhost
timezone=US/Pacific
network_interface=hme0 {netmask=255.255.255.0}
name_service=NONE
2.8 Add a host entry
Edit the /etc/ethers file and put a host entry for your client ;ethernet address followed by host name.
On client ok>banner will give ethernet address
#vi /etc/ethers
8:00:50:44:88:12 mercury
2.9 Adding a Client
The clients are added using add_install_client command . You have to be in the Tools directory of Solaris CD or image as the programme looks for the presence of valid Boot image dir in the same directory.
#cd /export/install/Solaris_2.7/Tools
#./add_install_client -e 8:00:50:44:88:12 -s jupiter:/export/install -c jupiter:/jumpstart -p jupiter:/jumpstart mercury sun4u
-e specify the ethernet address of client -s option specify the location of boot image ( As given in setup_install_server)
-c option specify the jumpstart directory path.
-p option specify the sysidcfg file location
jupiter is your jumpstart server
mercury is jumpstart client to be installed.
sun4u is the architecture of client
You need to enter the client through above command at the boot server also
3.0 Starting The client Installation
at client use the following command
ok>boot net – install
the system will initialize and starts booting from network
and you will see these messages
System is coming up
checking rules file
using profile any _machine
selecting cluster SUNWCall
Preparing system to install software
setting up disk
creating and checking up file systems
installing packages
After completion it will reboot and ask the new root password and after that takes you to the
console prompt where you can login and do additional task you want to do.
4.0 Begin & Finish Scripts
These are the optional features of jumpstart .
A begin script is a shell script which is used to perform the task before Solaris OS is installed. These are specified in the rules file.
These can be used for creating dynamic derived profiles or backing up files before upgrading.
A finish script is used to perform the tasks after the OS is installed but before reboot.
These can be used to customize root environment , adding patches , files etc.
These scripts can not be checked by the check script so it must be accurate.
Out put of these scripts goes to /var/adm/begin.log and finish.log.
These should be owned by the root with permission 644
5.0 Trouble Shooting
The following are a few of the common errors encountered in jumpstart.
Error : unknown client “client host name”
Source : add_install_client
Cause : host name can’t be resolved . check host entry is there in /etc/ethers or in nis/nis+ maps .
File just loaded does not appear to be executable .
Source : Solaris booting process
Cause : Improper media . Make sure proper media is available through disk image or CD in the install server . Also see
that the rules point to valid media type.
Warning : getfile:RPC failed : error 5 (RPC timed out)
Source: Client boot requests
Cause : Muliple entries for a client in different servers. There should not be multiple entries in different install server’s /etc/bootparams , /tftpboot or /rplboot . These causes a hang situation when all of them try to answer.
No network boot server .Unable to install the system. See installation instructions
Source : Client boot request.
Cause : Installation is not proper. Check the boot server installation again for any error in command or file .
Timeout waiting for ARP/RARP packet …
Source : Client boot request .
Cause : No server is answering its request for booting .Probably they don’t know about this client . See the proper entries are there in /etc/bootparams or nis maps with proper entries in nsswitch.conf . add_install_client is responsible for adding client information in jumpstart server so check the command and its option.
Tuesday, January 11, 2011
Solaris Performance Monitoring & Tuning – iostat, vmstat, netstat
Introduction to iostat , vmstat and netstat
This document is primarily written with reference to solaris performance monitoring and tuning but these tools are available in other unix variants also with slight syntax difference.
iostat , vmstat and netstat are three most commonly used tools for performance monitoring . These comes built in with the operating system and are easy to use .iostat stands for input output statistics and reports statistics for i/o devices such as disk drives . vmstat gives the statistics for virtual Memory and netstat gives the network statstics .
Following paragraphs describes these tools and their usage for performance monitoring.
Table of content :
1. Iostat
* Syntax
* example
* Result and Solutions
2. vmstat
* syntax
* example
* Result and Solutions
3. netstat
* syntax
* example
* Result and Solutions
Input Output statistics ( iostat )
iostat reports terminal and disk I/O activity and CPU utilization. The first line of output is for the time period since boot & each subsequent line is for the prior interval . Kernel maintains a number of counters to keep track of the values.
iostat’s activity class options default to tdc (terminal, disk, and CPU). If any other option/s are specified, this default is completely overridden i.e. iostat -d will report only statistics about the disks.
syntax:
Basic synctax is iostat interval count
option – let you specify the device for which information is needed like disk , cpu or terminal. (-d , -c , -t or -tdc ) . x options gives the extended statistics .
interval – is time period in seconds between two samples . iostat 4 will give data at each 4 seconds interval.
count – is the number of times the data is needed . iostat 4 5 will give data at 4 seconds interval 5 times
Example
$ iostat -xtc 5 2
extended disk statistics tty cpu
disk r/s w/s Kr/s Kw/s wait actv svc_t %w %b tin tout us sy wt id
sd0 2.6 3.0 20.7 22.7 0.1 0.2 59.2 6 19 0 84 3 85 11 0
sd1 4.2 1.0 33.5 8.0 0.0 0.2 47.2 2 23
sd2 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0 0
sd3 10.2 1.6 51.4 12.8 0.1 0.3 31.2 3 31
The fields have the following meanings:
disk name of the disk
r/s reads per second
w/s writes per second
Kr/s kilobytes read per second
Kw/s kilobytes written per second
wait average number of transactions waiting for service (Q length)
actv average number of transactions actively being serviced
(removed from the queue but not yet completed)
%w percent of time there are transactions waiting
for service (queue non-empty)
%b percent of time the disk is busy (transactions
in progress)
Results and Solutions
The values to look from the iostat output are:
* Reads/writes per second (r/s , w/s)
* Percentage busy (%b)
* Service time (svc_t)
If a disk shows consistently high reads/writes along with , the percentage busy (%b) of the disks is greater than 5 percent, and the average service time (svc_t) is greater than 30 milliseconds, then one of the following action needs to be taken
1.) Tune the application to use disk i/o more efficiently by modifying the disk queries and using available cache facilities of application servers .
2.) Spread the file system of the disk on to two or more disk using disk striping feature of volume manager /disksuite etc.
3.) Increase the system parameter values for inode cache , ufs_ninode , which is Number of inodes to be held in memory. Inodes are cached globally (for UFS), not on a per-file system basis
4.) Move the file system to another faster disk /controller or replace existing disk/controller to a faster one.
Virtual Memory Statistics ( vmstat )
vmstat – vmstat reports virtual memory statistics of process, virtual memory, disk, trap, and CPU activity.
On multicpu systems , vmstat averages the number of CPUs into the output. For per-process statistics .Without options, vmstat displays a one-line summary of the virtual memory activity since the system was booted.
syntax
Basic synctax is vmstat interval count
option – let you specify the type of information needed such as paging -p , cache -c ,.interrupt -i etc.
if no option is specified information about process , memory , paging , disk ,interrupts & cpu is displayed .
interval – is time period in seconds between two samples . vmstat 4 will give data at each 4 seconds interval.
count – is the number of times the data is needed . vmstat 4 5 will give data at 4 seconds interval 5 times.
Example
The following command displays a summary of what the system
is doing every five seconds.
example% vmstat 5
procs memory page disk faults cpu
r b w swap free re mf pi p fr de sr s0 s1 s2 s3 in sy cs us sy id
0 0 0 11456 4120 1 41 19 1 3 0 2 0 4 0 0 48 112 130 4 14 82
0 0 1 10132 4280 0 4 44 0 0 0 0 0 23 0 0 211 230 144 3 35 62
0 0 1 10132 4616 0 0 20 0 0 0 0 0 19 0 0 150 172 146 3 33 64
0 0 1 10132 5292 0 0 9 0 0 0 0 0 21 0 0 165 105 130 1 21 78
The fields of vmstat's display are
procs
r in run queue
b blocked for resources I/O, paging etc.
w swapped
memory (in Kbytes)
swap - amount of swap space currently available
free - size of the free list
page ( in units per second).
re page reclaims - see -S option for how this
field is modified.
mf minor faults - see -S option for how this
field is modified.
pi kilobytes paged in
po kilobytes paged out
fr kilobytes freed
de anticipated short-term memory shortfall (Kbytes)
sr pages scanned by clock algorithm
disk ( operations per second )
There are slots for up to four disks,
labeled with a single letter and number.
The letter indicates the type of disk
(s = SCSI, i = IPI, etc).
The number is the logical unit number.
faults
in (non clock) device interrupts
sy system calls
cs CPU context switches
cpu - breakdown of percentage usage of CPU time.
On multiprocessors this is an a
average across all processors.
us user time
sy system time
id idle time
Results and Solution from iostat
A. CPU issues
Following columns has to be watched to determine if there is any cpu issue
1. Processes in the run queue (procs r)
2. User time (cpu us)
3. System time (cpu sy)
4. Idle time (cpu id)
procs cpu
r b w us sy id
0 0 0 4 14 82
0 0 1 3 35 62
0 0 1 3 33 64
0 0 1 1 21 78
Problem symptoms
A.) Number of processes in run queue
1.) If the number of processes in run queue (procs r) are consistently greater than the number of CPUs on the system it will slow down system as there are more processes then available CPUs .
2.) if this number is more than four times the number of available CPUs in the system then system is facing shortage of cpu power and will greatly slow down the processess on the system.
3.) If the idle time (cpu id) is consistently 0 and if the system time (cpu sy) is double the user time (cpu us) system is facing shortage of CPU resources.
Resolution
Resolution to these kind of issues involves tuning of application procedures to make efficient use of cpu and as a last resort increasing the cpu power or adding more cpu to the system.
B. Memory Issues
Memory bottlenecks are determined by the scan rate (sr) . The scan rate is the pages scanned by the clock algorithm per second. If the scan rate (sr) is continuously over 200 pages per second then there is a memory shortage.
Resolution
1. Tune the applications & servers to make efficient use of memory and cache.
2. Increase system memory .
3. Implement priority paging in s in pre solaris 8 versions by adding line “set priority paging=1″ in
/etc/system. Remove this line if upgrading from Solaris 7 to 8 & retaining old /etc/system file.
Network Statistics (netstat)
netstat displays the contents of various network-related data structures in depending on the options selected.
Syntax
netstat
multiple options can be given at one time.
Options
-a – displays the state of all sockets.
-r – shows the system routing tables
-i – gives statistics on a per-interface basis.
-m – displays information from the network memory buffers. On Solaris, this shows statistics
for STREAMS
-p [proto] – retrieves statistics for the specified protocol
-s – shows per-protocol statistics. (some implementations allow -ss to remove fileds with a value of 0 (zero) from the display.)
-D – display the status of DHCP configured interfaces.
-n do not lookup hostnames, display only IP addresses.
-d (with -i) displays dropped packets per interface.
-I [interface] retrieve information about only the specified interface.
-v be verbose
interval – number for continuous display of statictics.
Example
$netstat -rn
Routing Table: IPv4
Destination Gateway Flags Ref Use Interface
-------------------- -------------------- ----- ----- ------ ---------
192.168.1.0 192.168.1.11 U 1 1444 le0
224.0.0.0 192.168.1.11 U 1 0 le0
default 192.168.1.1 UG 1 68276
127.0.0.1 127.0.0.1 UH 1 10497 lo0
This shows the output on a Solaris machine who’s IP address is 192.168.1.11 with a default router at 192.168.1.1
Results and Solutions
A.) Network availability
The command as above is mostly useful in troubleshooting network accessibility issues . When outside network is not accessible from a machine check the following
1. if the default router ip address is correct
2. you can ping it from your machine.
3. If router address is incorrect it can be changed with route add command. See man route for more information.
route command examples
$route add default
$route add 192.0.2.32
If the router address is correct but still you can’t ping it there may be some network cable /hub/switch problem and you have to try and eliminate the faulty component .
B.) Network Response
$ netstat -i
Name Mtu Net/Dest Address Ipkts Ierrs Opkts Oerrs Collis Queue
lo0 8232 loopback localhost 77814 0 77814 0 0 0
hme0 1500 server1 server1 10658 3 48325 0 279257 0
This option is used to diagnose the network problems when the connectivity is there but it is slow in response .
Values to look at:
* Collisions (Collis)
* Output packets (Opkts)
* Input errors (Ierrs)
* Input packets (Ipkts)
The above values will give information to workout
i. Network collision rate as follows :
Network collision rate = Output collision counts / Output packets
Network-wide collision rate greater than 10 percent will indicate
* Overloaded network,
* Poorly configured network,
* Hardware problems.
ii. Input packet error rate as follows :
Input Packet Error Rate = Ierrs / Ipkts.
If the input error rate is high (over 0.25 percent), the host is dropping packets. Hub/switch cables etc needs to be checked for potential problems.
C. Network socket & TCP Connection state
Netstat gives important information about network socket and tcp state . This is very useful in
finding out the open , closed and waiting network tcp connection .
Network states returned by netstat are following
CLOSED ---- Closed. The socket is not being used.
LISTEN ---- Listening for incoming connections.
SYN_SENT ---- Actively trying to establish connection.
SYN_RECEIVED ---- Initial synchronization of the connection under way.
ESTABLISHED ---- Connection has been established.
CLOSE_WAIT ---- Remote shut down; waiting for the socket to close.
FIN_WAIT_1 ---- Socket closed; shutting down connection.
CLOSING ---- Closed,
then remote shutdown; awaiting acknowledgement.
LAST_ACK ---- Remote shut down, then closed ;awaiting acknowledgement.
FIN_WAIT_2 ---- Socket closed; waiting for shutdown from remote.
TIME_WAIT ---- Wait after close for remote shutdown retransmission..
Example
#netstat -a
Local Address Remote Address Swind Send-Q Rwind Recv-Q State
*.* *.* 0 0 24576 0 IDLE
*.22 *.* 0 0 24576 0 LISTEN
*.22 *.* 0 0 24576 0 LISTEN
*.* *.* 0 0 24576 0 IDLE
*.32771 *.* 0 0 24576 0 LISTEN
*.4045 *.* 0 0 24576 0 LISTEN
*.25 *.* 0 0 24576 0 LISTEN
*.5987 *.* 0 0 24576 0 LISTEN
*.898 *.* 0 0 24576 0 LISTEN
*.32772 *.* 0 0 24576 0 LISTEN
*.32775 *.* 0 0 24576 0 LISTEN
*.32776 *.* 0 0 24576 0 LISTEN
*.* *.* 0 0 24576 0 IDLE
192.168.1.184.22 192.168.1.186.50457 41992 0 24616 0 ESTABLISHED
192.168.1.184.22 192.168.1.186.56806 38912 0 24616 0 ESTABLISHED
192.168.1.184.22 192.168.1.183.58672 18048 0 24616 0 ESTABLISHED
if you see a lots of connections in FIN_WAIT state tcp/ip parameters have to be tuned because the
connections are not being closed and they gets accumulating . After some time system may run out of
resource . TCP parameter can be tuned to define a time out so that connections can be released and used by new connection.
This document is primarily written with reference to solaris performance monitoring and tuning but these tools are available in other unix variants also with slight syntax difference.
iostat , vmstat and netstat are three most commonly used tools for performance monitoring . These comes built in with the operating system and are easy to use .iostat stands for input output statistics and reports statistics for i/o devices such as disk drives . vmstat gives the statistics for virtual Memory and netstat gives the network statstics .
Following paragraphs describes these tools and their usage for performance monitoring.
Table of content :
1. Iostat
* Syntax
* example
* Result and Solutions
2. vmstat
* syntax
* example
* Result and Solutions
3. netstat
* syntax
* example
* Result and Solutions
Input Output statistics ( iostat )
iostat reports terminal and disk I/O activity and CPU utilization. The first line of output is for the time period since boot & each subsequent line is for the prior interval . Kernel maintains a number of counters to keep track of the values.
iostat’s activity class options default to tdc (terminal, disk, and CPU). If any other option/s are specified, this default is completely overridden i.e. iostat -d will report only statistics about the disks.
syntax:
Basic synctax is iostat interval count
option – let you specify the device for which information is needed like disk , cpu or terminal. (-d , -c , -t or -tdc ) . x options gives the extended statistics .
interval – is time period in seconds between two samples . iostat 4 will give data at each 4 seconds interval.
count – is the number of times the data is needed . iostat 4 5 will give data at 4 seconds interval 5 times
Example
$ iostat -xtc 5 2
extended disk statistics tty cpu
disk r/s w/s Kr/s Kw/s wait actv svc_t %w %b tin tout us sy wt id
sd0 2.6 3.0 20.7 22.7 0.1 0.2 59.2 6 19 0 84 3 85 11 0
sd1 4.2 1.0 33.5 8.0 0.0 0.2 47.2 2 23
sd2 0.0 0.0 0.0 0.0 0.0 0.0 0.0 0 0
sd3 10.2 1.6 51.4 12.8 0.1 0.3 31.2 3 31
The fields have the following meanings:
disk name of the disk
r/s reads per second
w/s writes per second
Kr/s kilobytes read per second
Kw/s kilobytes written per second
wait average number of transactions waiting for service (Q length)
actv average number of transactions actively being serviced
(removed from the queue but not yet completed)
%w percent of time there are transactions waiting
for service (queue non-empty)
%b percent of time the disk is busy (transactions
in progress)
Results and Solutions
The values to look from the iostat output are:
* Reads/writes per second (r/s , w/s)
* Percentage busy (%b)
* Service time (svc_t)
If a disk shows consistently high reads/writes along with , the percentage busy (%b) of the disks is greater than 5 percent, and the average service time (svc_t) is greater than 30 milliseconds, then one of the following action needs to be taken
1.) Tune the application to use disk i/o more efficiently by modifying the disk queries and using available cache facilities of application servers .
2.) Spread the file system of the disk on to two or more disk using disk striping feature of volume manager /disksuite etc.
3.) Increase the system parameter values for inode cache , ufs_ninode , which is Number of inodes to be held in memory. Inodes are cached globally (for UFS), not on a per-file system basis
4.) Move the file system to another faster disk /controller or replace existing disk/controller to a faster one.
Virtual Memory Statistics ( vmstat )
vmstat – vmstat reports virtual memory statistics of process, virtual memory, disk, trap, and CPU activity.
On multicpu systems , vmstat averages the number of CPUs into the output. For per-process statistics .Without options, vmstat displays a one-line summary of the virtual memory activity since the system was booted.
syntax
Basic synctax is vmstat interval count
option – let you specify the type of information needed such as paging -p , cache -c ,.interrupt -i etc.
if no option is specified information about process , memory , paging , disk ,interrupts & cpu is displayed .
interval – is time period in seconds between two samples . vmstat 4 will give data at each 4 seconds interval.
count – is the number of times the data is needed . vmstat 4 5 will give data at 4 seconds interval 5 times.
Example
The following command displays a summary of what the system
is doing every five seconds.
example% vmstat 5
procs memory page disk faults cpu
r b w swap free re mf pi p fr de sr s0 s1 s2 s3 in sy cs us sy id
0 0 0 11456 4120 1 41 19 1 3 0 2 0 4 0 0 48 112 130 4 14 82
0 0 1 10132 4280 0 4 44 0 0 0 0 0 23 0 0 211 230 144 3 35 62
0 0 1 10132 4616 0 0 20 0 0 0 0 0 19 0 0 150 172 146 3 33 64
0 0 1 10132 5292 0 0 9 0 0 0 0 0 21 0 0 165 105 130 1 21 78
The fields of vmstat's display are
procs
r in run queue
b blocked for resources I/O, paging etc.
w swapped
memory (in Kbytes)
swap - amount of swap space currently available
free - size of the free list
page ( in units per second).
re page reclaims - see -S option for how this
field is modified.
mf minor faults - see -S option for how this
field is modified.
pi kilobytes paged in
po kilobytes paged out
fr kilobytes freed
de anticipated short-term memory shortfall (Kbytes)
sr pages scanned by clock algorithm
disk ( operations per second )
There are slots for up to four disks,
labeled with a single letter and number.
The letter indicates the type of disk
(s = SCSI, i = IPI, etc).
The number is the logical unit number.
faults
in (non clock) device interrupts
sy system calls
cs CPU context switches
cpu - breakdown of percentage usage of CPU time.
On multiprocessors this is an a
average across all processors.
us user time
sy system time
id idle time
Results and Solution from iostat
A. CPU issues
Following columns has to be watched to determine if there is any cpu issue
1. Processes in the run queue (procs r)
2. User time (cpu us)
3. System time (cpu sy)
4. Idle time (cpu id)
procs cpu
r b w us sy id
0 0 0 4 14 82
0 0 1 3 35 62
0 0 1 3 33 64
0 0 1 1 21 78
Problem symptoms
A.) Number of processes in run queue
1.) If the number of processes in run queue (procs r) are consistently greater than the number of CPUs on the system it will slow down system as there are more processes then available CPUs .
2.) if this number is more than four times the number of available CPUs in the system then system is facing shortage of cpu power and will greatly slow down the processess on the system.
3.) If the idle time (cpu id) is consistently 0 and if the system time (cpu sy) is double the user time (cpu us) system is facing shortage of CPU resources.
Resolution
Resolution to these kind of issues involves tuning of application procedures to make efficient use of cpu and as a last resort increasing the cpu power or adding more cpu to the system.
B. Memory Issues
Memory bottlenecks are determined by the scan rate (sr) . The scan rate is the pages scanned by the clock algorithm per second. If the scan rate (sr) is continuously over 200 pages per second then there is a memory shortage.
Resolution
1. Tune the applications & servers to make efficient use of memory and cache.
2. Increase system memory .
3. Implement priority paging in s in pre solaris 8 versions by adding line “set priority paging=1″ in
/etc/system. Remove this line if upgrading from Solaris 7 to 8 & retaining old /etc/system file.
Network Statistics (netstat)
netstat displays the contents of various network-related data structures in depending on the options selected.
Syntax
netstat
multiple options can be given at one time.
Options
-a – displays the state of all sockets.
-r – shows the system routing tables
-i – gives statistics on a per-interface basis.
-m – displays information from the network memory buffers. On Solaris, this shows statistics
for STREAMS
-p [proto] – retrieves statistics for the specified protocol
-s – shows per-protocol statistics. (some implementations allow -ss to remove fileds with a value of 0 (zero) from the display.)
-D – display the status of DHCP configured interfaces.
-n do not lookup hostnames, display only IP addresses.
-d (with -i) displays dropped packets per interface.
-I [interface] retrieve information about only the specified interface.
-v be verbose
interval – number for continuous display of statictics.
Example
$netstat -rn
Routing Table: IPv4
Destination Gateway Flags Ref Use Interface
-------------------- -------------------- ----- ----- ------ ---------
192.168.1.0 192.168.1.11 U 1 1444 le0
224.0.0.0 192.168.1.11 U 1 0 le0
default 192.168.1.1 UG 1 68276
127.0.0.1 127.0.0.1 UH 1 10497 lo0
This shows the output on a Solaris machine who’s IP address is 192.168.1.11 with a default router at 192.168.1.1
Results and Solutions
A.) Network availability
The command as above is mostly useful in troubleshooting network accessibility issues . When outside network is not accessible from a machine check the following
1. if the default router ip address is correct
2. you can ping it from your machine.
3. If router address is incorrect it can be changed with route add command. See man route for more information.
route command examples
$route add default
$route add 192.0.2.32
If the router address is correct but still you can’t ping it there may be some network cable /hub/switch problem and you have to try and eliminate the faulty component .
B.) Network Response
$ netstat -i
Name Mtu Net/Dest Address Ipkts Ierrs Opkts Oerrs Collis Queue
lo0 8232 loopback localhost 77814 0 77814 0 0 0
hme0 1500 server1 server1 10658 3 48325 0 279257 0
This option is used to diagnose the network problems when the connectivity is there but it is slow in response .
Values to look at:
* Collisions (Collis)
* Output packets (Opkts)
* Input errors (Ierrs)
* Input packets (Ipkts)
The above values will give information to workout
i. Network collision rate as follows :
Network collision rate = Output collision counts / Output packets
Network-wide collision rate greater than 10 percent will indicate
* Overloaded network,
* Poorly configured network,
* Hardware problems.
ii. Input packet error rate as follows :
Input Packet Error Rate = Ierrs / Ipkts.
If the input error rate is high (over 0.25 percent), the host is dropping packets. Hub/switch cables etc needs to be checked for potential problems.
C. Network socket & TCP Connection state
Netstat gives important information about network socket and tcp state . This is very useful in
finding out the open , closed and waiting network tcp connection .
Network states returned by netstat are following
CLOSED ---- Closed. The socket is not being used.
LISTEN ---- Listening for incoming connections.
SYN_SENT ---- Actively trying to establish connection.
SYN_RECEIVED ---- Initial synchronization of the connection under way.
ESTABLISHED ---- Connection has been established.
CLOSE_WAIT ---- Remote shut down; waiting for the socket to close.
FIN_WAIT_1 ---- Socket closed; shutting down connection.
CLOSING ---- Closed,
then remote shutdown; awaiting acknowledgement.
LAST_ACK ---- Remote shut down, then closed ;awaiting acknowledgement.
FIN_WAIT_2 ---- Socket closed; waiting for shutdown from remote.
TIME_WAIT ---- Wait after close for remote shutdown retransmission..
Example
#netstat -a
Local Address Remote Address Swind Send-Q Rwind Recv-Q State
*.* *.* 0 0 24576 0 IDLE
*.22 *.* 0 0 24576 0 LISTEN
*.22 *.* 0 0 24576 0 LISTEN
*.* *.* 0 0 24576 0 IDLE
*.32771 *.* 0 0 24576 0 LISTEN
*.4045 *.* 0 0 24576 0 LISTEN
*.25 *.* 0 0 24576 0 LISTEN
*.5987 *.* 0 0 24576 0 LISTEN
*.898 *.* 0 0 24576 0 LISTEN
*.32772 *.* 0 0 24576 0 LISTEN
*.32775 *.* 0 0 24576 0 LISTEN
*.32776 *.* 0 0 24576 0 LISTEN
*.* *.* 0 0 24576 0 IDLE
192.168.1.184.22 192.168.1.186.50457 41992 0 24616 0 ESTABLISHED
192.168.1.184.22 192.168.1.186.56806 38912 0 24616 0 ESTABLISHED
192.168.1.184.22 192.168.1.183.58672 18048 0 24616 0 ESTABLISHED
if you see a lots of connections in FIN_WAIT state tcp/ip parameters have to be tuned because the
connections are not being closed and they gets accumulating . After some time system may run out of
resource . TCP parameter can be tuned to define a time out so that connections can be released and used by new connection.
Solaris Network configuration
up Solaris networking often becomes challenging for the new sysadmins and new owners of Sun systems . This document details the steps involved in setting up of Solaris networking and can be used as a check list if you are already familiar with Solaris network configuration .
Table of contents :
1. Enable the network card
2. Configuring ipaddress and netmask and making the interface status as up .
3. Configuring Virtual interface :
4. Ip-forwarding
5. Router Configuration
6. Network Terms
7. Next Steps
Ifconfig command is used in Solaris to configure the network interfaces . The following lines describes the activities needed to configure a freshly installed network card from the root prompt .
1. Enable the network card
#ifconfig hme0 plumb
ifconfig -a command should show following type of output which means device is enabled and is ready to configure ip address and netmask :
hme0: flags=842 mtu 1500
inet 0.0.0.0 netmask 0
ether 3:22:11:6d:2e:1f
2. Configuring ipaddress and netmask and making the interface status as up .
#ifconfig hme0 192.9.2.106 netmask 255.255.255.0 up
#ifconfig -a will now show the ip address , netmask and up status as follows :
hme0: flags=843 mtu 1500
inet 192.9.2.106 netmask ffffff00 broadcast 192.9.2.255
ether 3:22:11:6d:2e:1f
The file /etc/netmasks is used to define netmasks for ip addresses .
127.0.0.1, is the standard loop back route and 127.0.0.0 is the default loopback ipaddress used by the kernel when no interface is configured this will be the only entry displayed by the system on invoking ifconfig -a command..
3. Configuring Virtual interface
Virtual interface can be configured to enable hme0 reply to more then one ip addresses. This is possible by using hme0 alias which can be configured by ifconfig command only . The new alias device name now becomes hme0:1 hme:2 etc.
#ifconfig hme0:1 172.40.30.4 netmask 255.255.0.0 up
ifconfig -a will show the original hme0 and alias interface :
hme0: flags=843 mtu 1500
inet 192.9.2.106 netmask ffffff00 broadcast 192.9.2.255
ether 3:22:11:6d:2e:1f
hme0:1: flags=842 mtu 1500
inet 172.40.30.4 netmask ffff0000 broadcast 172.40.255.255
4. Ip-forwarding
IP forwarding allows you to forward all requests coming for a certain port or URL to be redirected to a specified IP address.
ip forwarding becomes enabled automatically when system detects more then one interface at the booting time . The file involved is /etc/rc2.d/S69inet .
ipforwarding is on by default but can be turned off by following command :
#ndd -set /dev/ip ip_forwarding 0
5. Router Configuration
After interfaces and ipaddess have been configured the system needs a default router which will allow the machine to talk to world outside of local network .
You can specify a particular route for a particular address as in following example
#route add -net 10.0.0.0 -netmask 255.0.0.0 172.40.30.1 1
if the the destination ipaddess is not defined in this manner system forwards all requests to the default router .
default route is defined manually by editing /etc/defaultrouter file and putting router’s ipaddress entry in it. This file is read by /etc/rc2.d/S69inet file during the booting process and entry added to the routing table .
The route can be defined online also using routeadd command but the changes will be lost on reboot .To make changes permanent make sure to put an entry in /etc/defaultrouter.
#route add default 205.100.155.2 1
#route change default 205.100.155.2 1
The 1 at the end is the number of hops to the next gateway.
If an interface is not responding to the network, check to be sure it has the correct IP address and netmask , network cables are fine .
6. Network Terms
CIDR
CIDR : Classless Inter-Domain Routing – the notation often used instead of writing the subnet mask along with ip-address . It has network prefix at the end of a address as / number of network bits.This means that the IP address 192.200.20.10 with the subnet mask 255.255.255.0 can also be expressed as 192.200.20.10/24. The /24 indicates the network prefix length, which is equal to the number of continuous binary one-bits in the subnet mask (11111111.11111111.11111111.000000). Zeros are for addressing the hosts on this network.
VLSM
network can be variably subnetted into smaller networks, each smaller network having a different subnet mask .This functionality is avaiable in Solaris 2.6 above. the ipaddresses
Table of contents :
1. Enable the network card
2. Configuring ipaddress and netmask and making the interface status as up .
3. Configuring Virtual interface :
4. Ip-forwarding
5. Router Configuration
6. Network Terms
7. Next Steps
Ifconfig command is used in Solaris to configure the network interfaces . The following lines describes the activities needed to configure a freshly installed network card from the root prompt .
1. Enable the network card
#ifconfig hme0 plumb
ifconfig -a command should show following type of output which means device is enabled and is ready to configure ip address and netmask :
hme0: flags=842 mtu 1500
inet 0.0.0.0 netmask 0
ether 3:22:11:6d:2e:1f
2. Configuring ipaddress and netmask and making the interface status as up .
#ifconfig hme0 192.9.2.106 netmask 255.255.255.0 up
#ifconfig -a will now show the ip address , netmask and up status as follows :
hme0: flags=843 mtu 1500
inet 192.9.2.106 netmask ffffff00 broadcast 192.9.2.255
ether 3:22:11:6d:2e:1f
The file /etc/netmasks is used to define netmasks for ip addresses .
127.0.0.1, is the standard loop back route and 127.0.0.0 is the default loopback ipaddress used by the kernel when no interface is configured this will be the only entry displayed by the system on invoking ifconfig -a command..
3. Configuring Virtual interface
Virtual interface can be configured to enable hme0 reply to more then one ip addresses. This is possible by using hme0 alias which can be configured by ifconfig command only . The new alias device name now becomes hme0:1 hme:2 etc.
#ifconfig hme0:1 172.40.30.4 netmask 255.255.0.0 up
ifconfig -a will show the original hme0 and alias interface :
hme0: flags=843 mtu 1500
inet 192.9.2.106 netmask ffffff00 broadcast 192.9.2.255
ether 3:22:11:6d:2e:1f
hme0:1: flags=842 mtu 1500
inet 172.40.30.4 netmask ffff0000 broadcast 172.40.255.255
4. Ip-forwarding
IP forwarding allows you to forward all requests coming for a certain port or URL to be redirected to a specified IP address.
ip forwarding becomes enabled automatically when system detects more then one interface at the booting time . The file involved is /etc/rc2.d/S69inet .
ipforwarding is on by default but can be turned off by following command :
#ndd -set /dev/ip ip_forwarding 0
5. Router Configuration
After interfaces and ipaddess have been configured the system needs a default router which will allow the machine to talk to world outside of local network .
You can specify a particular route for a particular address as in following example
#route add -net 10.0.0.0 -netmask 255.0.0.0 172.40.30.1 1
if the the destination ipaddess is not defined in this manner system forwards all requests to the default router .
default route is defined manually by editing /etc/defaultrouter file and putting router’s ipaddress entry in it. This file is read by /etc/rc2.d/S69inet file during the booting process and entry added to the routing table .
The route can be defined online also using routeadd command but the changes will be lost on reboot .To make changes permanent make sure to put an entry in /etc/defaultrouter.
#route add default 205.100.155.2 1
#route change default 205.100.155.2 1
The 1 at the end is the number of hops to the next gateway.
If an interface is not responding to the network, check to be sure it has the correct IP address and netmask , network cables are fine .
6. Network Terms
CIDR
CIDR : Classless Inter-Domain Routing – the notation often used instead of writing the subnet mask along with ip-address . It has network prefix at the end of a address as / number of network bits.This means that the IP address 192.200.20.10 with the subnet mask 255.255.255.0 can also be expressed as 192.200.20.10/24. The /24 indicates the network prefix length, which is equal to the number of continuous binary one-bits in the subnet mask (11111111.11111111.11111111.000000). Zeros are for addressing the hosts on this network.
VLSM
network can be variably subnetted into smaller networks, each smaller network having a different subnet mask .This functionality is avaiable in Solaris 2.6 above. the ipaddresses
Backup commands – usage and examples
Backup commands – ufsdump, tar , cpio
Unix backup and restore can be done using unix commands ufsdump , tar ,
cpio . Though these commands may be sufficient for small setups in
order to take a enterprise backup you have to go in for some custom
backup and restore solutions like Symatic netbackup, EMC networker or
Amanda .
Any backup solution using these commands depends on the type of backup you
are taking and capability of the commands to fulfill the requirement . Following
paragraphs will give you an idea of commands , syntax and examples.
Features of ufsdump , tar , cpio
ufsdump
1. Used for complete file system backup .
2. It copies every thing from regular files in a file system to special character and block device files.
2. It can work on mounted or unmounted file systems.
tar:
1. Used for single or multiple files backup .
2. Can’t backup special character & block device files ( 0 byte files ).
3. Works only on mounted file system.
cpio:
1. Used for single or multiple files backup .
2. Can backup special character & block device files .
3. Works only on mounted file system.
4. Need a list of files to be backed up .
5. Preserve hard links and time stamps of the files .
Identifying the tape device in Solaris
dmesg | grep st
Checking the status of the tape drive
mt -f /dev/rmt/0 status
Backup restore and disk copy with ufsdump :
Backup file system using ufsdump
ufsdump 0cvf /dev/rmt/0 /dev/rdsk/c0t0d0s0
or
ufsdump 0cvf /dev/rmt/0 /usr
To restore a dump with ufsrestore
ufsrestore rvf /dev/rmt/0
ufsrestore in interactive mode allowing selection of individual files and
directories using add , ls , cd , pwd and extract commands .
ufsrestore -i /dev/rmt/0
Making a copy of a disk slice using ufsdump
ufsdump 0f – /dev/rdsk/c0t0d0s7 |(cd /mnt/backup ;ufsrestore xf -)
Backup restore and disk copy with tar :
– Backing up all files in a directory including subdirectories to a tape device (/dev/rmt/0),
tar cvf /dev/rmt/0 *
Viewing a tar backup on a tape
tar tvf /dev/rmt/0
Extracting tar backup from the tape
tar xvf /dev/rmt/0
(Restoration will go to present directory or original backup path depending on
relative or absolute path names used for backup )
Backup restore and disk copy with tar :
Back up all the files in current directory to tape .
find . -depth -print | cpio -ovcB > /dev/rmt/0
cpio expects a list of files and find command provides the list , cpio has
to put these file on some destination and a > sign redirect these files to tape . This can be a file as well .
Viewing cpio files on a tape
cpio -ivtB < /dev/rmt/0
Restoring a cpio backup
cpio -ivcB < /dev/rmt/0
Compress/uncompress files :
You may have to compress the files before or after the backup and it can be done with following commands .
Compressing a file
compress -v file_name
gzip filename
To uncompress a file
uncompress file_name.Z
or
gunzip filename
Unix backup and restore can be done using unix commands ufsdump , tar ,
cpio . Though these commands may be sufficient for small setups in
order to take a enterprise backup you have to go in for some custom
backup and restore solutions like Symatic netbackup, EMC networker or
Amanda .
Any backup solution using these commands depends on the type of backup you
are taking and capability of the commands to fulfill the requirement . Following
paragraphs will give you an idea of commands , syntax and examples.
Features of ufsdump , tar , cpio
ufsdump
1. Used for complete file system backup .
2. It copies every thing from regular files in a file system to special character and block device files.
2. It can work on mounted or unmounted file systems.
tar:
1. Used for single or multiple files backup .
2. Can’t backup special character & block device files ( 0 byte files ).
3. Works only on mounted file system.
cpio:
1. Used for single or multiple files backup .
2. Can backup special character & block device files .
3. Works only on mounted file system.
4. Need a list of files to be backed up .
5. Preserve hard links and time stamps of the files .
Identifying the tape device in Solaris
dmesg | grep st
Checking the status of the tape drive
mt -f /dev/rmt/0 status
Backup restore and disk copy with ufsdump :
Backup file system using ufsdump
ufsdump 0cvf /dev/rmt/0 /dev/rdsk/c0t0d0s0
or
ufsdump 0cvf /dev/rmt/0 /usr
To restore a dump with ufsrestore
ufsrestore rvf /dev/rmt/0
ufsrestore in interactive mode allowing selection of individual files and
directories using add , ls , cd , pwd and extract commands .
ufsrestore -i /dev/rmt/0
Making a copy of a disk slice using ufsdump
ufsdump 0f – /dev/rdsk/c0t0d0s7 |(cd /mnt/backup ;ufsrestore xf -)
Backup restore and disk copy with tar :
– Backing up all files in a directory including subdirectories to a tape device (/dev/rmt/0),
tar cvf /dev/rmt/0 *
Viewing a tar backup on a tape
tar tvf /dev/rmt/0
Extracting tar backup from the tape
tar xvf /dev/rmt/0
(Restoration will go to present directory or original backup path depending on
relative or absolute path names used for backup )
Backup restore and disk copy with tar :
Back up all the files in current directory to tape .
find . -depth -print | cpio -ovcB > /dev/rmt/0
cpio expects a list of files and find command provides the list , cpio has
to put these file on some destination and a > sign redirect these files to tape . This can be a file as well .
Viewing cpio files on a tape
cpio -ivtB < /dev/rmt/0
Restoring a cpio backup
cpio -ivcB < /dev/rmt/0
Compress/uncompress files :
You may have to compress the files before or after the backup and it can be done with following commands .
Compressing a file
compress -v file_name
gzip filename
To uncompress a file
uncompress file_name.Z
or
gunzip filename
Checking and Repairing Unix File system with fsck
fsck is a Unix utility for checking and repairing file system inconsistencies . File system can become inconsistent due to several reasons and the most common is abnormal shutdown due to hardware failure , power failure or switching off the system without proper shutdown. Due to these reasons the superblock in a file system is not updated and has mismatched information relating to system data blocks, free blocks and inodes .
fsck – Modes of operation :
fsck operates in two modes interactive and non interactive :
Interactive – fsck examines the file system and stops at each error it finds in the file system and gives the problem description and ask for user response whether to correct the problem or continue without making any change to the file system.
Non interactive :fsck tries to repair all the problems it finds in a file system without stopping for user response useful in case of a large number of inconsistencies in a file system but has the disadvantage of removing some useful files which are detected to be corrupt .
If file system is found to have problem at the booting time non interactive fsck is run and all errors which are considered safe to correct are corrected. But if still file system has problems the system boots in single user mode asking for user to manually run the fsck to correct the problems in file system
Running fsck :
fsck should always be run in a single user mode which ensures proper repair of file system . If it is run in a busy system where the file system is changing constantly fsck may see the changes as inconsistencies and may corrupt the file system .
If the system can not be brought in a single user mode fsck should be run on the partitions ,other than root & usr , after unmounting them . Root & usr partitions can not be unmounted . If the system fails to come up due to root/usr files system corruption the system can be booted with CD and root/usr partitions can be repaired using fsck.
command syntax
fsck [ -F fstype] [-V] [-yY] [-o options] special
-F fstype type of file system to be repaired ( ufs , vxfs etc)
-V verify the command line syntax but do not run the command
-y or -Y Run the command in non interactive mode – repair all errors encountered without waiting for user response.
-o options Three options can be specified with -o flag
b=n where n is the number of next super block if primary super block is corrupted in a file system .
p option used to make safe repair options during the booting process.
f force the file system check regardless of its clean flag.
special – Block or character device name of the file system to be checked/repaired – for example /dev/rdsk/c0t3d0s4 .Character device should be used for consistencies check & repair
fsck phases
fsck checks the file system in a series of 5 pages and checks a specific functionality of file system in each phase.
** phase 1 – Check Blocks and Sizes
** phase 2 – Check Pathnames
** phase 3 – Check Connectivity
** phase 4 – Check Reference Counts
** phase 5 – Check Cylinder Groups
fsck error messages & Corrective action :
1. Corrupted superblock – fsck fails to run
If the superblock is corrupted the file system still can be repaired using alternate superblock which are formed while making new file system .
the first alternate superblock number is 32 and others superblock numbers can be found using the following command :
newfs -N /dev/rdsk/c0t0d0s6
for example to run fsck using first alternate superblock following command is used
fsck -F ufs -o b=32 /dev/rdsk/c0t0d0s6
2. Link counter adjustment
fsck finds mismatch between directory inode link counts and actual directory links and prompts for adjustment in case of interactive operation. Link count adjustments are considered to be a safe operation in a file system and should be repaired by giving ‘y’ response to the adjust ? prompt during fsck.
3. Free Block count salvage
During fsck the number of free blocks listed in a superblock and actual unallocated free blocks count does not match. fsck inform this mismatch and asks to salvage free block count to synchronize the superblock count. This error can be corrected without any potential problem to the file system or files.
4. Unreferenced file reconnection
While checking connectivity fsck finds some inodes which are allocated but not referenced – not attached to any directory . Answering y to reconnect message by fsck links these files to the lost+found directory with their inode number as their name .
To get more info about the files in lost+found ‘file’ command can be used to see the type of files and subsequently they can be opened in their applications or text editors to find out about their contents. If the file is found to be correct it can be used after copying to some other directory and renaming it.
fsck – Modes of operation :
fsck operates in two modes interactive and non interactive :
Interactive – fsck examines the file system and stops at each error it finds in the file system and gives the problem description and ask for user response whether to correct the problem or continue without making any change to the file system.
Non interactive :fsck tries to repair all the problems it finds in a file system without stopping for user response useful in case of a large number of inconsistencies in a file system but has the disadvantage of removing some useful files which are detected to be corrupt .
If file system is found to have problem at the booting time non interactive fsck is run and all errors which are considered safe to correct are corrected. But if still file system has problems the system boots in single user mode asking for user to manually run the fsck to correct the problems in file system
Running fsck :
fsck should always be run in a single user mode which ensures proper repair of file system . If it is run in a busy system where the file system is changing constantly fsck may see the changes as inconsistencies and may corrupt the file system .
If the system can not be brought in a single user mode fsck should be run on the partitions ,other than root & usr , after unmounting them . Root & usr partitions can not be unmounted . If the system fails to come up due to root/usr files system corruption the system can be booted with CD and root/usr partitions can be repaired using fsck.
command syntax
fsck [ -F fstype] [-V] [-yY] [-o options] special
-F fstype type of file system to be repaired ( ufs , vxfs etc)
-V verify the command line syntax but do not run the command
-y or -Y Run the command in non interactive mode – repair all errors encountered without waiting for user response.
-o options Three options can be specified with -o flag
b=n where n is the number of next super block if primary super block is corrupted in a file system .
p option used to make safe repair options during the booting process.
f force the file system check regardless of its clean flag.
special – Block or character device name of the file system to be checked/repaired – for example /dev/rdsk/c0t3d0s4 .Character device should be used for consistencies check & repair
fsck phases
fsck checks the file system in a series of 5 pages and checks a specific functionality of file system in each phase.
** phase 1 – Check Blocks and Sizes
** phase 2 – Check Pathnames
** phase 3 – Check Connectivity
** phase 4 – Check Reference Counts
** phase 5 – Check Cylinder Groups
fsck error messages & Corrective action :
1. Corrupted superblock – fsck fails to run
If the superblock is corrupted the file system still can be repaired using alternate superblock which are formed while making new file system .
the first alternate superblock number is 32 and others superblock numbers can be found using the following command :
newfs -N /dev/rdsk/c0t0d0s6
for example to run fsck using first alternate superblock following command is used
fsck -F ufs -o b=32 /dev/rdsk/c0t0d0s6
2. Link counter adjustment
fsck finds mismatch between directory inode link counts and actual directory links and prompts for adjustment in case of interactive operation. Link count adjustments are considered to be a safe operation in a file system and should be repaired by giving ‘y’ response to the adjust ? prompt during fsck.
3. Free Block count salvage
During fsck the number of free blocks listed in a superblock and actual unallocated free blocks count does not match. fsck inform this mismatch and asks to salvage free block count to synchronize the superblock count. This error can be corrected without any potential problem to the file system or files.
4. Unreferenced file reconnection
While checking connectivity fsck finds some inodes which are allocated but not referenced – not attached to any directory . Answering y to reconnect message by fsck links these files to the lost+found directory with their inode number as their name .
To get more info about the files in lost+found ‘file’ command can be used to see the type of files and subsequently they can be opened in their applications or text editors to find out about their contents. If the file is found to be correct it can be used after copying to some other directory and renaming it.
Securing Solaris
your system from internal & external security vulnerabilities
Introduction
Solaris security broadly falls under two groups – one is where the system is accessible using local area network/vlan and it has to be secured against unauthorized access. Second is system is accessible over the Internet to a number of persons and it has to be protected against unauthorized access using network or security loopholes.
This document details some of the focus areas for security and provides suggestions to make it strong.
Following topics are covered in this article for securing Solaris .
1. Latest patches
2. Access to the system.
3. Run level and network services
4. ip module
5. System file , /etc/system
6. sadmind daemon
7. root kit & srload hack
1. Latest patches
Any operating system might have security bugs, which are detected only when system is used in a real time environment. Apply whatever patches are available as of to date to plug the already discovered security loopholes and look for the information about new security related bugs.
Generally it takes some time when security loophole is discovered and its patch is developed . So the best strategy against such situations is to keep informed by reading security related bulletin of the OS vendor and disabling the affected service or constantly monitoring it and applying patches whenever its available .
A perl script – patchk – is available at sunsolve.sun.com which can be used to identify & compare the existing patches and download the latest ones.
2. Access to the system
Limit Root Access
Limit the direct root access by making sure console entry in /etc/default/login is not commented out .
If secure shell is being used to access the systems edit sshd.config and ssh.config to disable root access
sshd.config
Permit root login no
Permit empty password no
Allow hosts
Allow users
ssh.config
Forward x11 no
Password authentication no
Host based authentication is more secure as it is based on private keys and public keys and only user with the keys are allowed to connect . Password authentication is less secure as they can be guessed or cracked by some programs .
Limit su capabilities
Allow only a few selected members of a group to use su to prevent any unauthorized access by guessing the root password . Create a system administrator’s group and change su owner to root and group to administrator’s group . Change su permissions to allow only member of this group an execute permission .
Remote Access files
.rhosts ,.netrc hosts.equivalent are the files that provides access to the remote systems and should be monitored carefully .They should be checked regularly for any unauthorized entry or if not needed can be made with zero permission – chmod 0 . This will not allow creation of new file by the same name and put entries to gain access.
Keep access log
sulog file gives information about su login attempts to the system similarly a loginlog file can be created by touching /etc/loginlog which keeps all the login information . Besides last command also give useful information about the persons accessing the system.
3. Run level and network services
Stop unnecessary services at run levels:
/etc/rc2.d and /etc/rc3.d directories have scripts starting at the booting time or when run level is changed . By default a number of services are started out of which only a few might be required . In most of the cases , particularly in production environment certain services are not required at all but provides various ports for gaining entry to the system
Evaluate your system requirements and look at the rc scripts , disable the files that are not required by making letter capital in the beginning as ‘s’ . System requirements may vary from system to system but you should check if you don’t need following services & can disable them.
Enabled Disabled
S71ldap.client S72autoinstall
S72slpd S88sendmail S72nfs.client S74autofs S99dtlogin S15nfs.server s71ldap.client s72autoinstall
s72slpd s88sendmail s73nfs.client s1574autofs s99dtlogin s15nfs.server
Stop unnecessary and insecure network services
/etc/inetd.conf has entry for about fifty network services and most of them are started by default . While some of these services are not secure -telnet,ftp ,some of it are not required at all . These services can allow a intruder to get in by providing system information and ports.
Services such as finger ,sysstat & netstat provide useful information about the users , system and network. Depending on the applications requirement some of these services should be stopped by commenting out corresponding entry in /etc/inetd.conf
ftp should be disabled and secure copy ,scp ,sftp should be used instead . But if you must use ftp then limit the users which can do a ftp to the system . /etc/ftpusers file can be created to keep the ftp user list .
4. ip module
Control the IP Behavior :
IP module can be tuned to prevent forwarding , redirecting of packets and request for information from the system . These parameters can be set using ndd with the given value to limit these features .
#ndd -set /dev/ip ip_forward_directed_broadcasts 0
#ndd -set /dev/ip ip_forward_src_routed 0
#ndd -set /dev/ip ip_ignore_redirect 1
#ndd -set /dev/ip ip_ire_flush_interval 60000
#ndd -set /dev/ip ip_ire_arp_interval 60000
#ndd -set /dev/ip ip_respond_to_echo_broadcast 0
#ndd -set /dev/ip ip_respond_to_timestamp 0
#ndd -set /dev/ip ip_respond_to_timestamp_broadcast 0
#ndd -set /dev/ip ip_send_redirects 0
To see a list of all parameter for a particular driver
#ndd /dev/ip
name to get/set ? ?
To get value of a particular parameter :
#ndd -get /dev/ip ip_respond_to_timestamp_broadcast
5. System file , /etc/system
Add the following lines to /etc/system file to prevent the buffer overflow in a possible attack to execute some malicious code on your machine.
set noexec_user_stack=1
set noexec_user_stack_log=1
Depending upon the requirement all or a combination of all the above suggestions can be implemented . Certain application software, web servers etc have there own parameters for securing access and data . So besides solaris those parameters may have to be taken in consideration in addition to solaris parameters to secure system completely.
6. sadmind daemon vulnerability
The sadmind daemon is used for distributed system administration operations in the Solstice AdminSuite applications. In its default configuration sadmind uses a set of clear text Remote Procedure Calls (RPC) to authenticate between two machines. An attacker can construct RPC packets that allow them r to forge a valid client identity and get it validated . Once the sadmind client has authenticated, the hacker can perform any command on the remote system even with root privileges .
Protecting against sadmind vulnerability
sadmind is controlled through the file /etc/inetd.conf as per the following entry :
100232/10 tli rpc/udp wait root /usr/sbin/sadmind sadmind
In this configuration, sadmind uses cleartext hostnames and authentication credentials as the security level is default no security level .
There are two ways to deal with this situation :
1. Completely disable the sadmind in the inted.conf if not required by commenting out the sadmind line or removing it altogather .
#100232/10 tli rpc/udp wait root /usr/sbin/sadmind sadmind
Restart inetd:
# /usr/bin/pkill -HUP inetd
2. Increase the level of security by requiring DES encryption for your authentication mechanism by adding the ‘-S 2′ flag to the end of the sadmind line in inetd.conf:
100232/10 tli rpc/udp wait root /usr/sbin/sadmind sadmind -S 2
Restart inetd:
# /usr/bin/pkill -HUP inetd
7. Root Kit
The hackers in some cases installs a “root” kit which changes various files in the system in order to gain super user privileges and to conceal the compromise.
You can determine with pkgchk command if certain files have changed :
/bin/su
/usr/sbin/ping
/usr/bin/du
/usr/bin/passwd
/usr/bin/find
/bin/ls
/bin/netstat
/usr/bin/strings
If there is any error reported on any of these files then system is compromised . The best resort in these cases is to take system off the network and do a fresh operating system installation .
srload :
srload is a part of root kit which is used to get the non-standard SSH port access by the attackers . Compromised systems have a entry in /etc/inittab of following line
SV:23:respawn:/usr/bin/srload -D -q
and may have the following file modified along with other files :
/etc/rcS.d/S30rootusr.sh
The immediate action for this is to disable the srload command by removing it from /etc/inittab after booting in single user mode and removing srload command binary from /usr/bin or any other location .
Introduction
Solaris security broadly falls under two groups – one is where the system is accessible using local area network/vlan and it has to be secured against unauthorized access. Second is system is accessible over the Internet to a number of persons and it has to be protected against unauthorized access using network or security loopholes.
This document details some of the focus areas for security and provides suggestions to make it strong.
Following topics are covered in this article for securing Solaris .
1. Latest patches
2. Access to the system.
3. Run level and network services
4. ip module
5. System file , /etc/system
6. sadmind daemon
7. root kit & srload hack
1. Latest patches
Any operating system might have security bugs, which are detected only when system is used in a real time environment. Apply whatever patches are available as of to date to plug the already discovered security loopholes and look for the information about new security related bugs.
Generally it takes some time when security loophole is discovered and its patch is developed . So the best strategy against such situations is to keep informed by reading security related bulletin of the OS vendor and disabling the affected service or constantly monitoring it and applying patches whenever its available .
A perl script – patchk – is available at sunsolve.sun.com which can be used to identify & compare the existing patches and download the latest ones.
2. Access to the system
Limit Root Access
Limit the direct root access by making sure console entry in /etc/default/login is not commented out .
If secure shell is being used to access the systems edit sshd.config and ssh.config to disable root access
sshd.config
Permit root login no
Permit empty password no
Allow hosts
Allow users
ssh.config
Forward x11 no
Password authentication no
Host based authentication is more secure as it is based on private keys and public keys and only user with the keys are allowed to connect . Password authentication is less secure as they can be guessed or cracked by some programs .
Limit su capabilities
Allow only a few selected members of a group to use su to prevent any unauthorized access by guessing the root password . Create a system administrator’s group and change su owner to root and group to administrator’s group . Change su permissions to allow only member of this group an execute permission .
Remote Access files
.rhosts ,.netrc hosts.equivalent are the files that provides access to the remote systems and should be monitored carefully .They should be checked regularly for any unauthorized entry or if not needed can be made with zero permission – chmod 0 . This will not allow creation of new file by the same name and put entries to gain access.
Keep access log
sulog file gives information about su login attempts to the system similarly a loginlog file can be created by touching /etc/loginlog which keeps all the login information . Besides last command also give useful information about the persons accessing the system.
3. Run level and network services
Stop unnecessary services at run levels:
/etc/rc2.d and /etc/rc3.d directories have scripts starting at the booting time or when run level is changed . By default a number of services are started out of which only a few might be required . In most of the cases , particularly in production environment certain services are not required at all but provides various ports for gaining entry to the system
Evaluate your system requirements and look at the rc scripts , disable the files that are not required by making letter capital in the beginning as ‘s’ . System requirements may vary from system to system but you should check if you don’t need following services & can disable them.
Enabled Disabled
S71ldap.client S72autoinstall
S72slpd S88sendmail S72nfs.client S74autofs S99dtlogin S15nfs.server s71ldap.client s72autoinstall
s72slpd s88sendmail s73nfs.client s1574autofs s99dtlogin s15nfs.server
Stop unnecessary and insecure network services
/etc/inetd.conf has entry for about fifty network services and most of them are started by default . While some of these services are not secure -telnet,ftp ,some of it are not required at all . These services can allow a intruder to get in by providing system information and ports.
Services such as finger ,sysstat & netstat provide useful information about the users , system and network. Depending on the applications requirement some of these services should be stopped by commenting out corresponding entry in /etc/inetd.conf
ftp should be disabled and secure copy ,scp ,sftp should be used instead . But if you must use ftp then limit the users which can do a ftp to the system . /etc/ftpusers file can be created to keep the ftp user list .
4. ip module
Control the IP Behavior :
IP module can be tuned to prevent forwarding , redirecting of packets and request for information from the system . These parameters can be set using ndd with the given value to limit these features .
#ndd -set /dev/ip ip_forward_directed_broadcasts 0
#ndd -set /dev/ip ip_forward_src_routed 0
#ndd -set /dev/ip ip_ignore_redirect 1
#ndd -set /dev/ip ip_ire_flush_interval 60000
#ndd -set /dev/ip ip_ire_arp_interval 60000
#ndd -set /dev/ip ip_respond_to_echo_broadcast 0
#ndd -set /dev/ip ip_respond_to_timestamp 0
#ndd -set /dev/ip ip_respond_to_timestamp_broadcast 0
#ndd -set /dev/ip ip_send_redirects 0
To see a list of all parameter for a particular driver
#ndd /dev/ip
name to get/set ? ?
To get value of a particular parameter :
#ndd -get /dev/ip ip_respond_to_timestamp_broadcast
5. System file , /etc/system
Add the following lines to /etc/system file to prevent the buffer overflow in a possible attack to execute some malicious code on your machine.
set noexec_user_stack=1
set noexec_user_stack_log=1
Depending upon the requirement all or a combination of all the above suggestions can be implemented . Certain application software, web servers etc have there own parameters for securing access and data . So besides solaris those parameters may have to be taken in consideration in addition to solaris parameters to secure system completely.
6. sadmind daemon vulnerability
The sadmind daemon is used for distributed system administration operations in the Solstice AdminSuite applications. In its default configuration sadmind uses a set of clear text Remote Procedure Calls (RPC) to authenticate between two machines. An attacker can construct RPC packets that allow them r to forge a valid client identity and get it validated . Once the sadmind client has authenticated, the hacker can perform any command on the remote system even with root privileges .
Protecting against sadmind vulnerability
sadmind is controlled through the file /etc/inetd.conf as per the following entry :
100232/10 tli rpc/udp wait root /usr/sbin/sadmind sadmind
In this configuration, sadmind uses cleartext hostnames and authentication credentials as the security level is default no security level .
There are two ways to deal with this situation :
1. Completely disable the sadmind in the inted.conf if not required by commenting out the sadmind line or removing it altogather .
#100232/10 tli rpc/udp wait root /usr/sbin/sadmind sadmind
Restart inetd:
# /usr/bin/pkill -HUP inetd
2. Increase the level of security by requiring DES encryption for your authentication mechanism by adding the ‘-S 2′ flag to the end of the sadmind line in inetd.conf:
100232/10 tli rpc/udp wait root /usr/sbin/sadmind sadmind -S 2
Restart inetd:
# /usr/bin/pkill -HUP inetd
7. Root Kit
The hackers in some cases installs a “root” kit which changes various files in the system in order to gain super user privileges and to conceal the compromise.
You can determine with pkgchk command if certain files have changed :
/bin/su
/usr/sbin/ping
/usr/bin/du
/usr/bin/passwd
/usr/bin/find
/bin/ls
/bin/netstat
/usr/bin/strings
If there is any error reported on any of these files then system is compromised . The best resort in these cases is to take system off the network and do a fresh operating system installation .
srload :
srload is a part of root kit which is used to get the non-standard SSH port access by the attackers . Compromised systems have a entry in /etc/inittab of following line
SV:23:respawn:/usr/bin/srload -D -q
and may have the following file modified along with other files :
/etc/rcS.d/S30rootusr.sh
The immediate action for this is to disable the srload command by removing it from /etc/inittab after booting in single user mode and removing srload command binary from /usr/bin or any other location .
Solaris Installation
Solaris installation poses a challenges to the new Solaris sysadmins who have never done the installation of Solaris before . Though the installation itself is simple and straight forward but doing it the first time comes with its own anxiety associated with unexplored and unknown things .
The idea of this article is to introduce you with the procedure and sequence of event Solaris installation to build enough confidence to finish the installation on your own.
Table of contents
1. Before you begin
2. Getting Started
3. Starting the installation
4. OS distributions & disk configuration
5. After Installation
6. Next Steps
1. Before you begin
For Solaris installation on standalone Sun machine you need the following besides sun cpu :
A) Sun Monitor and Sun Keyboard
OR
For carrying the installation through the serial port A of Sun (ttya)
Dumb Terminal or PC with serial port communication software like HyperTerminal
AND
A null modem cable ( Pin 2 & 3 crossed 5 common ground in 9 Pin to 9 pin ; Pin 7 is common ground in 25 Pin connector ) connecting sun’s serial port A with PC serial port.
B) You will also require a IP address, netmask and a host name for your system.
2. Getting Started
Installation starts at OK> prompt & you can get to ok> using any of the following method :
A. by pressing Stop A key sequence on a Sun Keyboard.
B. typing #init 0 if your system boots up directly .
C. Pressing ctrl-break or shift-break on a pc keyboard if using pc as
console through serial port.
D. If auto-boot feature is enabled system directly boots up
and gives you a # prompt .You can disable auto-boot so next time it
stays at ok prompt for starting installation.
#/usr/platform/sun4u/bin/eeprom auto-boot?=false
reboot the system.
3. Starting the installation
Insert the installation media – OS CD in CD drive and type boot cdrom at ok> prompt .
Ok>boot cdrom
The first phase begins with system identification and gathers information about the system from the the user .System starts booting up and after initialization it asks for language and locale also terminal type in case of PC/terminal
Select your locale and DEC VT100 terminal type for terminal selection
Further installation through the terminal require response to the
selections through ESC and function keys and space bar which are
mentioned on the installation screen.
On the next screens, you are to identify the system as networked or non-networked, and set the default time zone and date/time. After this following host information is required :
A) A host name for the system
B) Whether the system is networked if yes you will have to
provide the IP address & netmask of this machine.
Next you will be asked to select the name services
Name services
[ ] NIS+
[ ] NIS
[ ] DNS
[X ] None
Select the service if you have complete details like domain names etc or select none to configure after installation.
You have to select a distribution type from among the choices choices
4. OS distribution & Disk configuration
After identification is complete the installation process proceeds on to the OS and disk configuration and need your input for these settings. Selection depends on role of your machine
Typical space requirement for Solaris 7 is given here.
[ ] Entire Distribution plus OEM support 64-bit 1242.00 MB (F4 to Customize
[X] Entire Distribution 64-bit .....…...….1215.00 MB
[ ] Developer System Support 64-bit.... 1154.00 MB
[ ] End User System Support 64-bit .….. 765.00 MB
[ ] Core System Support .............. .334.00 MB
* Entire distribution with OEM has all software with some third party software
* Entire distribution has all software without third party software .
* Developer system has run time libraries for C software etc.
* End user has X windows and CDE environment .
* Core system is without X windows softwares etc.
If you are not sure select entire distribution.
You will be presented with choice to select the boot disk among the disks present in the system ,unless you have reasons select the c0t0d0 at boot disk.
[ X ] c0t0d0 (17269 MB) boot disk 17269 MB
[ ] c0t1d0 (17269 MB) 17269 MB
overlap partition represents entire disk and is slice s2 of the disk.
If any of the disk contain a preexisting partition you will be given a choice to preserve the partition .
Next the current layout is given ( if existing ) and you are asked to select between Automatic and Custom layout of disk partitions.
* Automatic layout make a single partition of entire boot disk .
* Customize option gives and option to create the partitions and select the sizes .
Things to keep in mind while doing interactive or custom installation
- Additional space is required in /var & /home if server is to handle mail and printing as mail and print files are formed in /var & if the user home directories are to be located on /home partition
A sample partition table may look like following .
File system/Mount point Disk/Slice Size
---------------------------------------
/ c0t0d0s0 300 MB
swap c0t0d0s1 2000 MB
overlap c0t0d0s2 17269 MB
/usr c0t0d0s3 2000 MB
/opt c0t0d0s4 1000 MB
/var c0t0d0s5 1000 MB
- The swap partition size depends on the size of RAM in the system if you are not sure of its size keep it double the RAM or more than RAM in the system.
- If you are not sure of individual partition sizes of / , /usr /opt & /var make one partition as / and keep its size sufficiently higher than the distribution size you have selected in earlier steps . Always keep in mind the future software that you might have to install like compilers applications etc and log files that will be generated and accumulate in /var directory or partition.
After you have specified the partition sizes it gives summary and error if any
Installation Option: Initial
Boot Device: c0t0d0s0
Client Services: None
Software: Solaris 2.7, Entire Distribution
File System and Disk Layout:
/ c0t0d0s0 300 MB
swap c0t0d0s1 2000 MB
/usr c0t0d0s3 2000 MB
/opt c0t0d0s4 1000 MB
/var c0t0d0s5 1000 MB
one more question is asked about rebooting
[X] Auto Reboot
[ ] Manual Reboot
Afterwards it starts configuring disk making partitions and installing software indicating the progress in a table .
MBytes Installed: 700.66
MBytes Remaining: 0.00
Installing:
| | | | | |
0 20 40 60 80 100
After the installation is complete it customizes system files , devices ,logs , installs patches which are there in OS CD for that release. You can install recommended latest patches later
System then reboots or ask you to reboot depending upon the choice selected earlier .
5. After Installation
After rebooting it asks for new root passed and comes to console prompt where you can login as root install patches ,additional software , make user etc. etc.
The idea of this article is to introduce you with the procedure and sequence of event Solaris installation to build enough confidence to finish the installation on your own.
Table of contents
1. Before you begin
2. Getting Started
3. Starting the installation
4. OS distributions & disk configuration
5. After Installation
6. Next Steps
1. Before you begin
For Solaris installation on standalone Sun machine you need the following besides sun cpu :
A) Sun Monitor and Sun Keyboard
OR
For carrying the installation through the serial port A of Sun (ttya)
Dumb Terminal or PC with serial port communication software like HyperTerminal
AND
A null modem cable ( Pin 2 & 3 crossed 5 common ground in 9 Pin to 9 pin ; Pin 7 is common ground in 25 Pin connector ) connecting sun’s serial port A with PC serial port.
B) You will also require a IP address, netmask and a host name for your system.
2. Getting Started
Installation starts at OK> prompt & you can get to ok> using any of the following method :
A. by pressing Stop A key sequence on a Sun Keyboard.
B. typing #init 0 if your system boots up directly .
C. Pressing ctrl-break or shift-break on a pc keyboard if using pc as
console through serial port.
D. If auto-boot feature is enabled system directly boots up
and gives you a # prompt .You can disable auto-boot so next time it
stays at ok prompt for starting installation.
#/usr/platform/sun4u/bin/eeprom auto-boot?=false
reboot the system.
3. Starting the installation
Insert the installation media – OS CD in CD drive and type boot cdrom at ok> prompt .
Ok>boot cdrom
The first phase begins with system identification and gathers information about the system from the the user .System starts booting up and after initialization it asks for language and locale also terminal type in case of PC/terminal
Select your locale and DEC VT100 terminal type for terminal selection
Further installation through the terminal require response to the
selections through ESC and function keys and space bar which are
mentioned on the installation screen.
On the next screens, you are to identify the system as networked or non-networked, and set the default time zone and date/time. After this following host information is required :
A) A host name for the system
B) Whether the system is networked if yes you will have to
provide the IP address & netmask of this machine.
Next you will be asked to select the name services
Name services
[ ] NIS+
[ ] NIS
[ ] DNS
[X ] None
Select the service if you have complete details like domain names etc or select none to configure after installation.
You have to select a distribution type from among the choices choices
4. OS distribution & Disk configuration
After identification is complete the installation process proceeds on to the OS and disk configuration and need your input for these settings. Selection depends on role of your machine
Typical space requirement for Solaris 7 is given here.
[ ] Entire Distribution plus OEM support 64-bit 1242.00 MB (F4 to Customize
[X] Entire Distribution 64-bit .....…...….1215.00 MB
[ ] Developer System Support 64-bit.... 1154.00 MB
[ ] End User System Support 64-bit .….. 765.00 MB
[ ] Core System Support .............. .334.00 MB
* Entire distribution with OEM has all software with some third party software
* Entire distribution has all software without third party software .
* Developer system has run time libraries for C software etc.
* End user has X windows and CDE environment .
* Core system is without X windows softwares etc.
If you are not sure select entire distribution.
You will be presented with choice to select the boot disk among the disks present in the system ,unless you have reasons select the c0t0d0 at boot disk.
[ X ] c0t0d0 (17269 MB) boot disk 17269 MB
[ ] c0t1d0 (17269 MB) 17269 MB
overlap partition represents entire disk and is slice s2 of the disk.
If any of the disk contain a preexisting partition you will be given a choice to preserve the partition .
Next the current layout is given ( if existing ) and you are asked to select between Automatic and Custom layout of disk partitions.
* Automatic layout make a single partition of entire boot disk .
* Customize option gives and option to create the partitions and select the sizes .
Things to keep in mind while doing interactive or custom installation
- Additional space is required in /var & /home if server is to handle mail and printing as mail and print files are formed in /var & if the user home directories are to be located on /home partition
A sample partition table may look like following .
File system/Mount point Disk/Slice Size
---------------------------------------
/ c0t0d0s0 300 MB
swap c0t0d0s1 2000 MB
overlap c0t0d0s2 17269 MB
/usr c0t0d0s3 2000 MB
/opt c0t0d0s4 1000 MB
/var c0t0d0s5 1000 MB
- The swap partition size depends on the size of RAM in the system if you are not sure of its size keep it double the RAM or more than RAM in the system.
- If you are not sure of individual partition sizes of / , /usr /opt & /var make one partition as / and keep its size sufficiently higher than the distribution size you have selected in earlier steps . Always keep in mind the future software that you might have to install like compilers applications etc and log files that will be generated and accumulate in /var directory or partition.
After you have specified the partition sizes it gives summary and error if any
Installation Option: Initial
Boot Device: c0t0d0s0
Client Services: None
Software: Solaris 2.7, Entire Distribution
File System and Disk Layout:
/ c0t0d0s0 300 MB
swap c0t0d0s1 2000 MB
/usr c0t0d0s3 2000 MB
/opt c0t0d0s4 1000 MB
/var c0t0d0s5 1000 MB
one more question is asked about rebooting
[X] Auto Reboot
[ ] Manual Reboot
Afterwards it starts configuring disk making partitions and installing software indicating the progress in a table .
MBytes Installed: 700.66
MBytes Remaining: 0.00
Installing:
| | | | | |
0 20 40 60 80 100
After the installation is complete it customizes system files , devices ,logs , installs patches which are there in OS CD for that release. You can install recommended latest patches later
System then reboots or ask you to reboot depending upon the choice selected earlier .
5. After Installation
After rebooting it asks for new root passed and comes to console prompt where you can login as root install patches ,additional software , make user etc. etc.
Crontab – Quick Reference
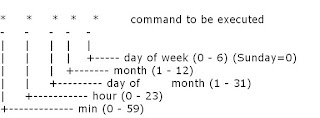
Setting up cron jobs in Unix and Solaris
cron is a unix, solaris utility that allows tasks to be automatically run in the background at regular intervals by the cron daemon. These tasks are often termed as cron jobs in unix , solaris. Crontab (CRON TABle) is a file which contains the schedule of cron entries to be run and at specified times.
This document covers following aspects of Unix cron jobs
1. Crontab Restrictions
2. Crontab Commands
3. Crontab file – syntax
4. Crontab Example
5. Crontab Environment
6. Disable Email
7. Generate log file for crontab activity
1. Crontab Restrictions
You can execute crontab if your name appears in the file /usr/lib/cron/cron.allow. If that file does not exist, you can use
crontab if your name does not appear in the file /usr/lib/cron/cron.deny.
If only cron.deny exists and is empty, all users can use crontab. If neither file exists, only the root user can use crontab. The allow/deny files consist of one user name per line.
2. Crontab Commands
export EDITOR=vi ;to specify a editor to open crontab file.
crontab -e Edit your crontab file, or create one if it doesn’t already exist.
crontab -l Display your crontab file.
crontab -r Remove your crontab file.
crontab -v Display the last time you edited your crontab file. (This option is only available on a few systems.)
3. Crontab file
Crontab syntax :
A crontab file has five fields for specifying day , date and time followed by the command to be run at that interval.
* in the value field above means all legal values as in braces for that column.
The value column can have a * or a list of elements separated by commas. An element is either a number in the ranges shown above or two numbers in the range separated by a hyphen (meaning an inclusive range).
Notes
A. ) Repeat pattern like /2 for every 2 minutes or /10 for every 10 minutes is not supported by all operating systems. If you try to use it and crontab complains it is probably not supported.
B.) The specification of days can be made in two fields: month day and weekday. If both are specified in an entry, they are cumulative meaning both of the entries will get executed .
4. Crontab Example
A line in crontab file like below removes the tmp files from /home/someuser/tmp each day at 6:30 PM.
30 18 * * * rm /home/someuser/tmp/*
Changing the parameter values as below will cause this command to run at different time schedule below :
min hour day/month month day/week Execution time
30 0 1 1,6,12 * – 00:30 Hrs on 1st of Jan, June & Dec.
0 20 * 10 1-5 –8.00 PM every weekday (Mon-Fri) only in Oct.
0 0 1,10,15 * * – midnight on 1st ,10th & 15th of month
5,10 0 10 * 1 – At 12.05,12.10 every Monday & on 10th of every month
:
Note : If you inadvertently enter the crontab command with no argument(s), do not attempt to get out with Control-d. This removes all entries in your crontab file. Instead, exit with Control-c.
5. Crontab Environment
cron invokes the command from the user’s HOME directory with the shell, (/usr/bin/sh).
cron supplies a default environment for every shell, defining:
HOME=user’s-home-directory
LOGNAME=user’s-login-id
PATH=/usr/bin:/usr/sbin:.
SHELL=/usr/bin/sh
Users who desire to have their .profile executed must explicitly do so in the crontab entry or in a script called by the entry.
6. Disable Email
By default cron jobs sends a email to the user account executing the cronjob. If this is not needed put the following command At the end of the cron job line .
>/dev/null 2>&1
7. Generate log file
To collect the cron execution execution log in a file :
30 18 * * * rm /home/someuser/tmp/* > /home/someuser/cronlogs/clean_tmp_dir.log
Subscribe to:
Posts (Atom)